Recent Posts
Archives
Using AWS Secrets Manager In AWS CodeBuild: A Beginner’s Guide
In today’s dynamic development landscape, where safeguarding sensitive information is paramount, AWS CodeBuild stands out as a reliable solution for building and deploying applications. Elevating your security game becomes seamless with AWS Secrets Manager integration. Let’s embark on a journey to fortify your AWS CodeBuild pipeline by effortlessly managing secrets with AWS Secrets Manager.
Understanding the Power of AWS Secrets Manager
AWS Secrets Manager is your go-to ally for centralizing and securing crucial information like API keys and database credentials. With automatic rotation and straightforward integration, it simplifies the entire secrets lifecycle management process. For more details: AWS Secret Manager
Why This Matters:
- Centralized Security Hub: Securely store and manage all your secrets in one centralized location.
- Automated Rotation: Effortlessly enhance security by automating the rotation of sensitive data.
- Seamless Integration: Integrate AWS Secrets Manager seamlessly into AWS CodeBuild for a cohesive and secure development pipeline.
Step-by-Step Guide for Seamless Integration:
Step 1: Create a Secret
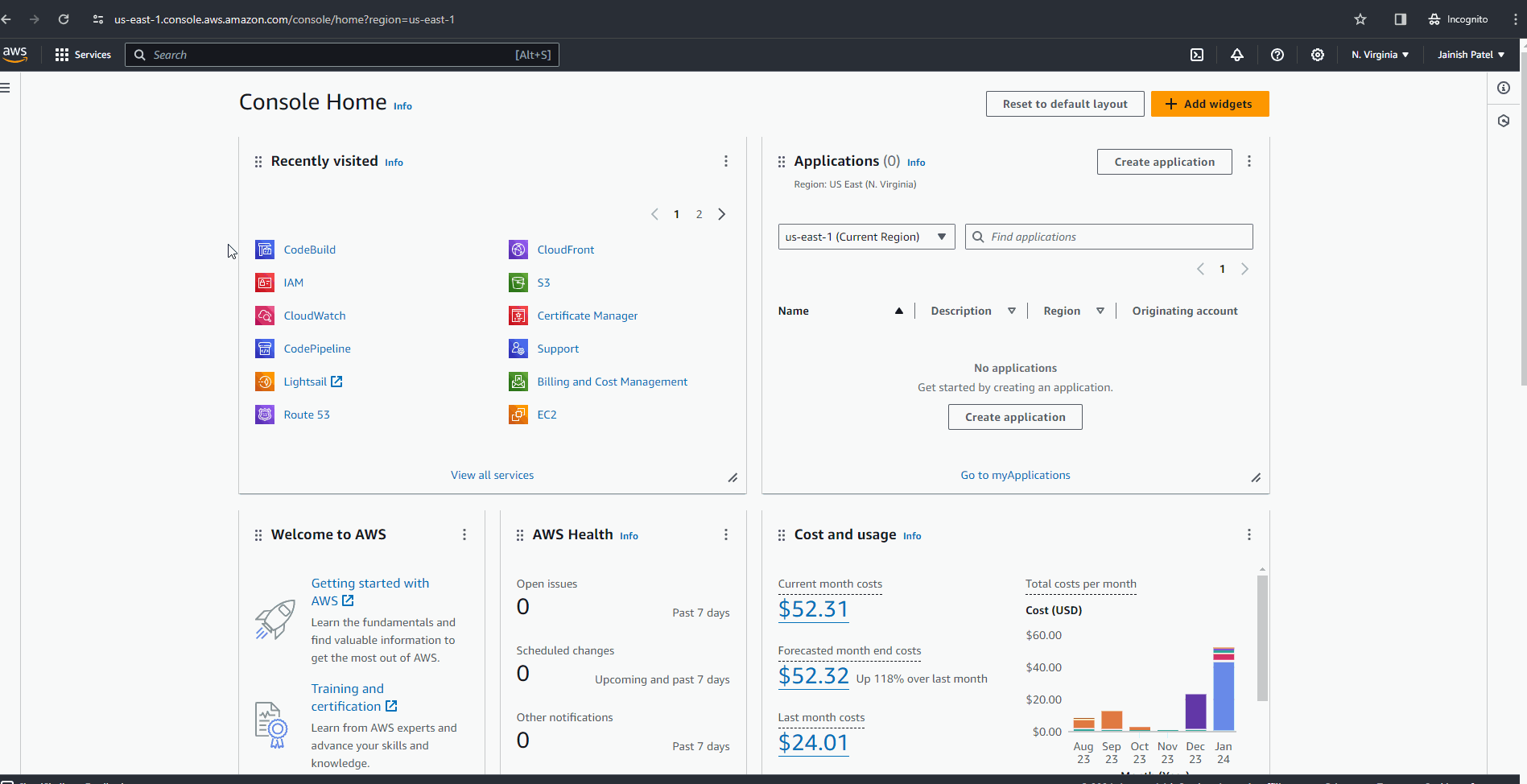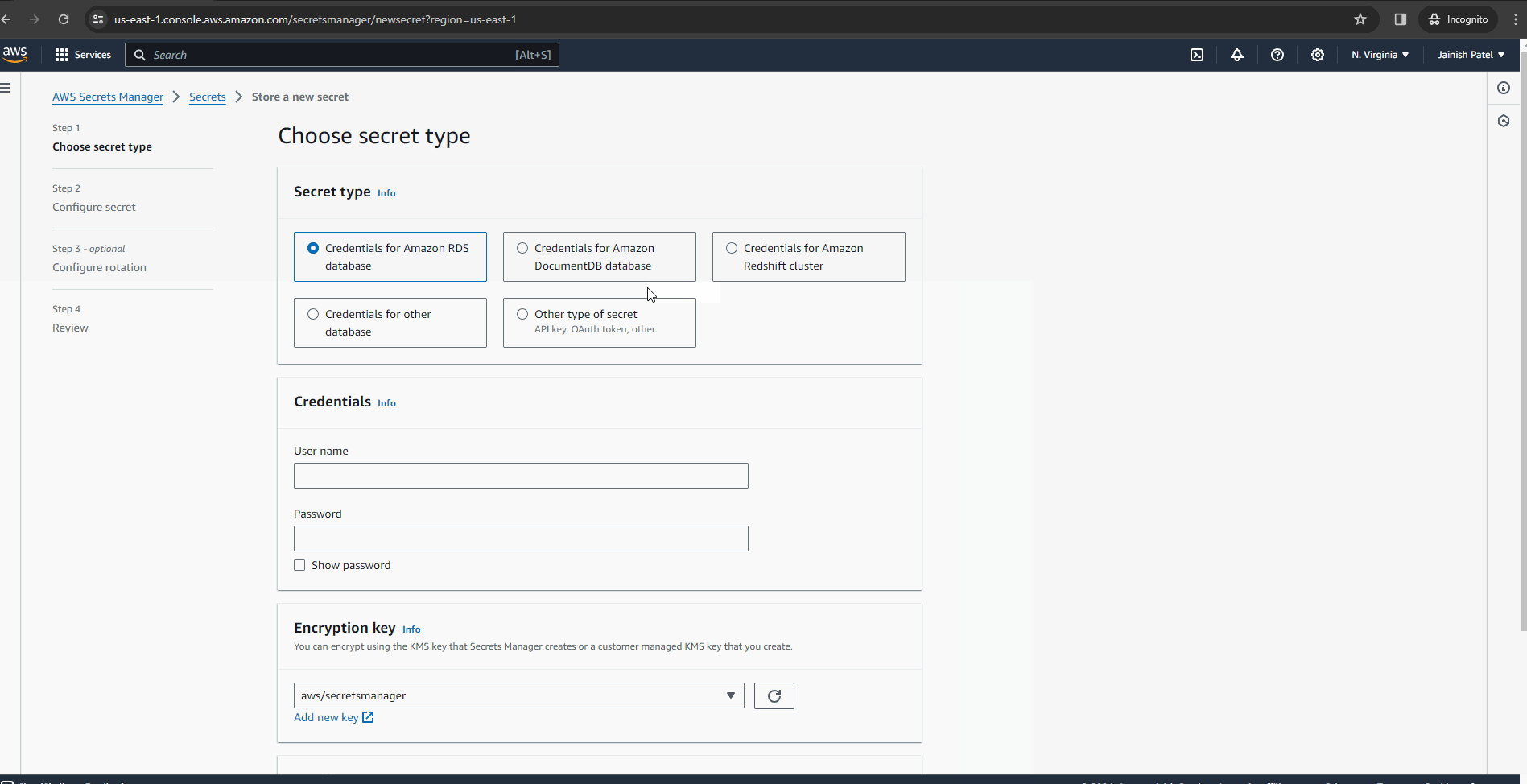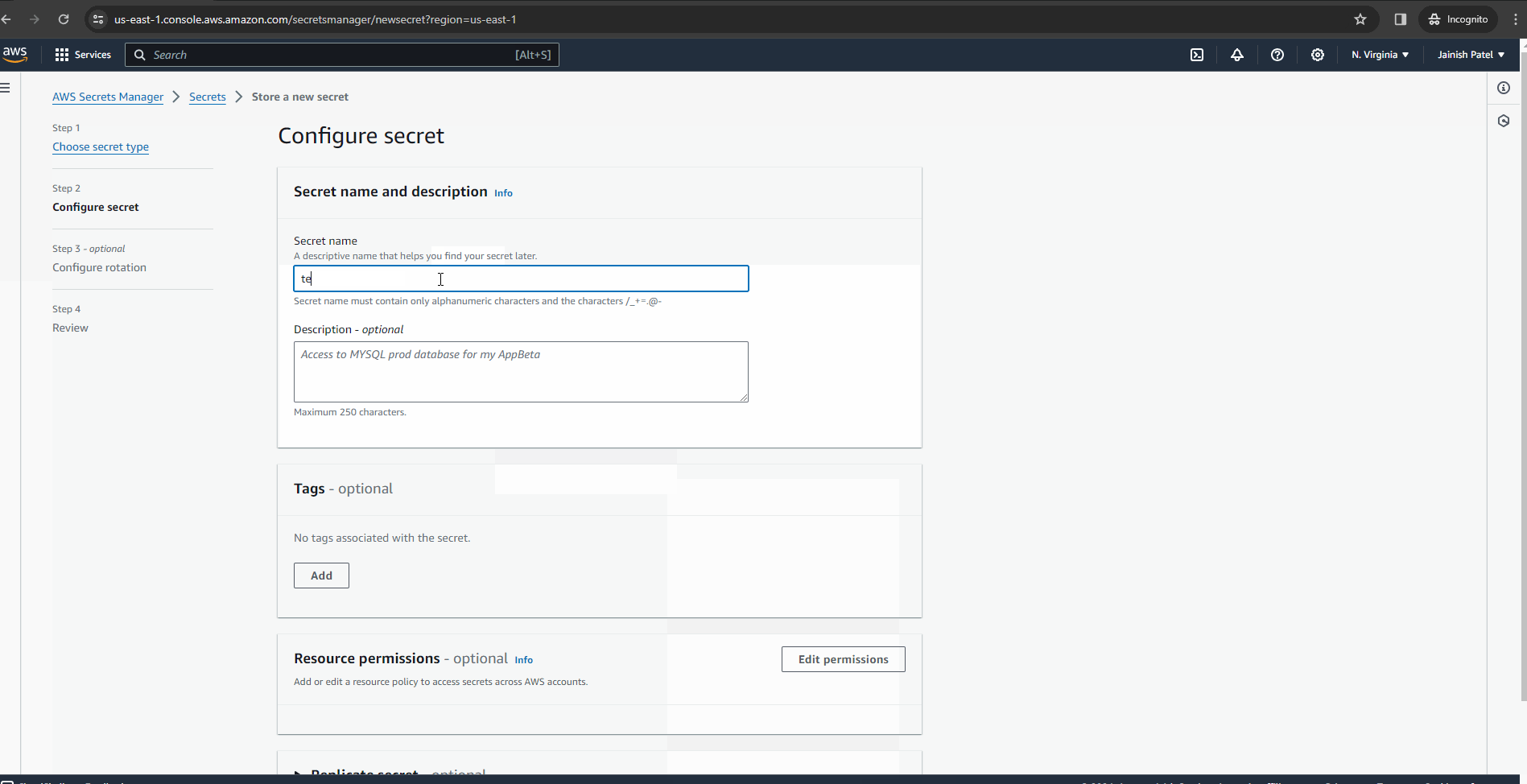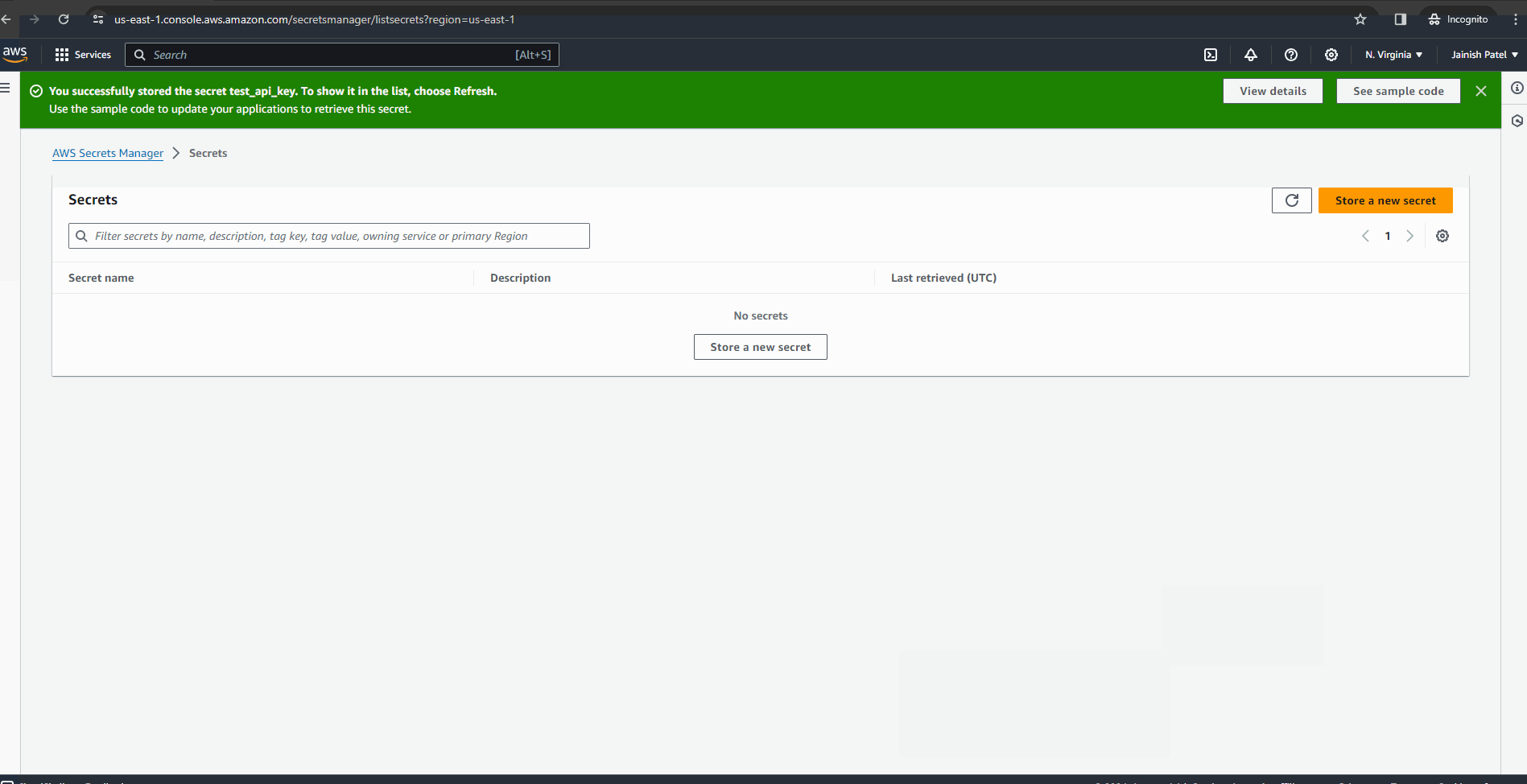
Kickstart by logging into the AWS Management Console. Head to AWS Secrets Manager, initiating the creation of a secret – be it database credentials, API keys, or a custom key-value pair tailored to your build process needs.
Step 2: Provide CodeBuild Access to Secrets
Transitioning to the next phase, enhance the security of your build process by updating the IAM role of your Build project. By incorporating the permission provided below, you guarantee that your AWS CodeBuild project possesses the essential authorizations to access the secret manager. If you require guidance on creating the CodeBuild project itself, refer to our detailed blog for assistance.
{
"Version":"2012-10-17",
"Statement":[
{
"Effect":"Allow",
"Action":[
"secretsmanager:GetSecretValue"
],
"Resource":[
"arn:aws:secretsmanager:us-east-1:123456789123:secret:test_api_key-*"
]
}
]
}Expert Tip:
Substitute the Resource ARN in the policy with the format “arn:aws:secretsmanager:<AWS::Region>:<AWS::AccountID>:secret:<SecretName>-*“. The * is included at the end because, when creating the Secret Manager, AWS automatically appends a random string to the Resource ARN by default.
Step 3: Refine Build Specification
Enhance your build specification file (buildspec.yml) by incorporating logic for fetching and utilizing secrets. Two options are available:
Option 1 :
version: 0.2
env:
secrets-manager:
api_key: "test_api_key:api_key"
# <Variable Name>: "<SecretName>:<SecretKey>:<Version(optiional)>"
# You can add multiple variables if you are fetching multiple SecretKey.
phases:
build:
commands:
- echo "API Key value is $api_key."Pros:
- No need for JQ library; simplifies JSON extraction.
- Echo statements are restricted, enhancing security practices.
Cons:
- Requires manual version updates for Secret Manager versioning.
Outcome :
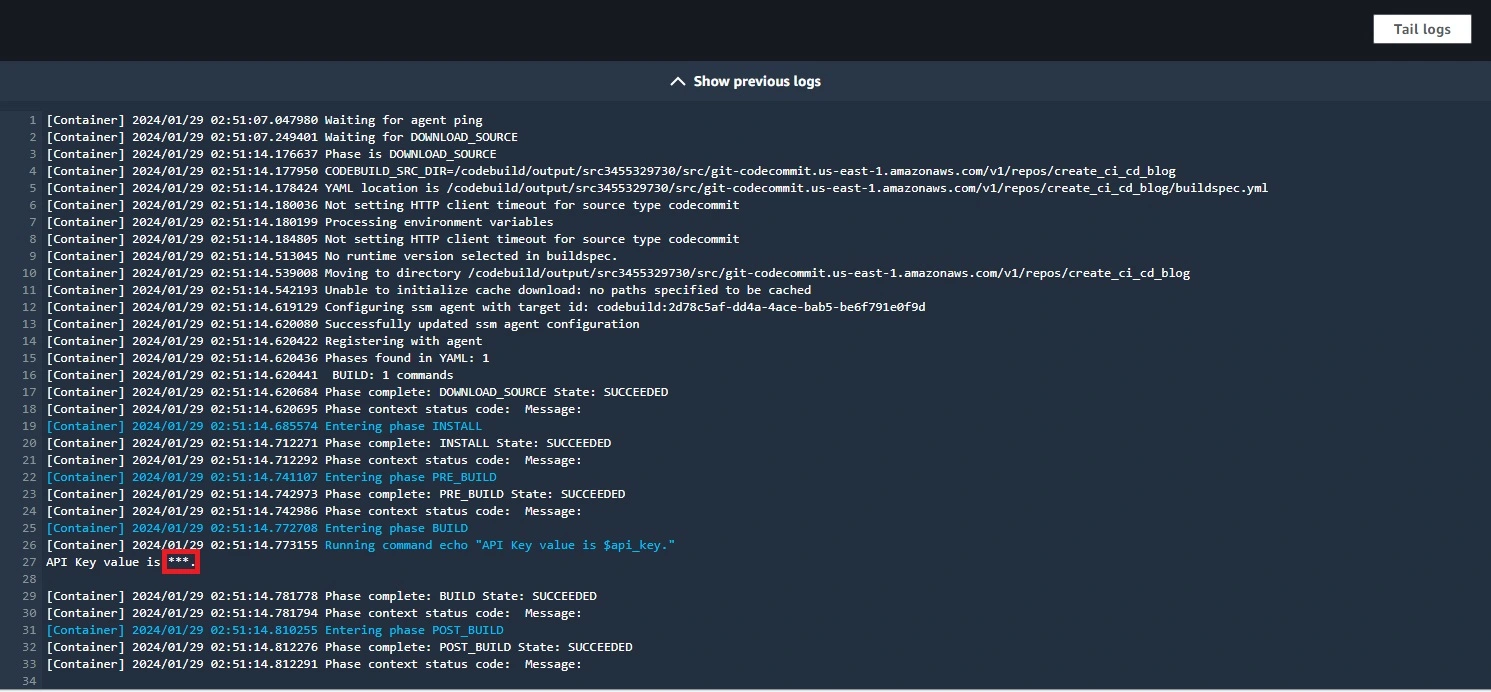
Option 2 :
version: 0.2
phases:
build:
commands:
- echo "Fetching secrets from AWS Secrets Manager"
- |
Secrets=$(aws secretsmanager get-secret-value --secret-id test_api_key --query SecretString --output text)
export api_key_value=$(echo $Secrets | jq -r '.api_key')
- echo "API Key value is $api_key_value."Pros:
- Utilizes AWS CLI for dynamic secret fetching.
- Consistent retrieval of the latest version.
Cons:
- Potential security risk with values being printed and stored in logs.
Outcome :
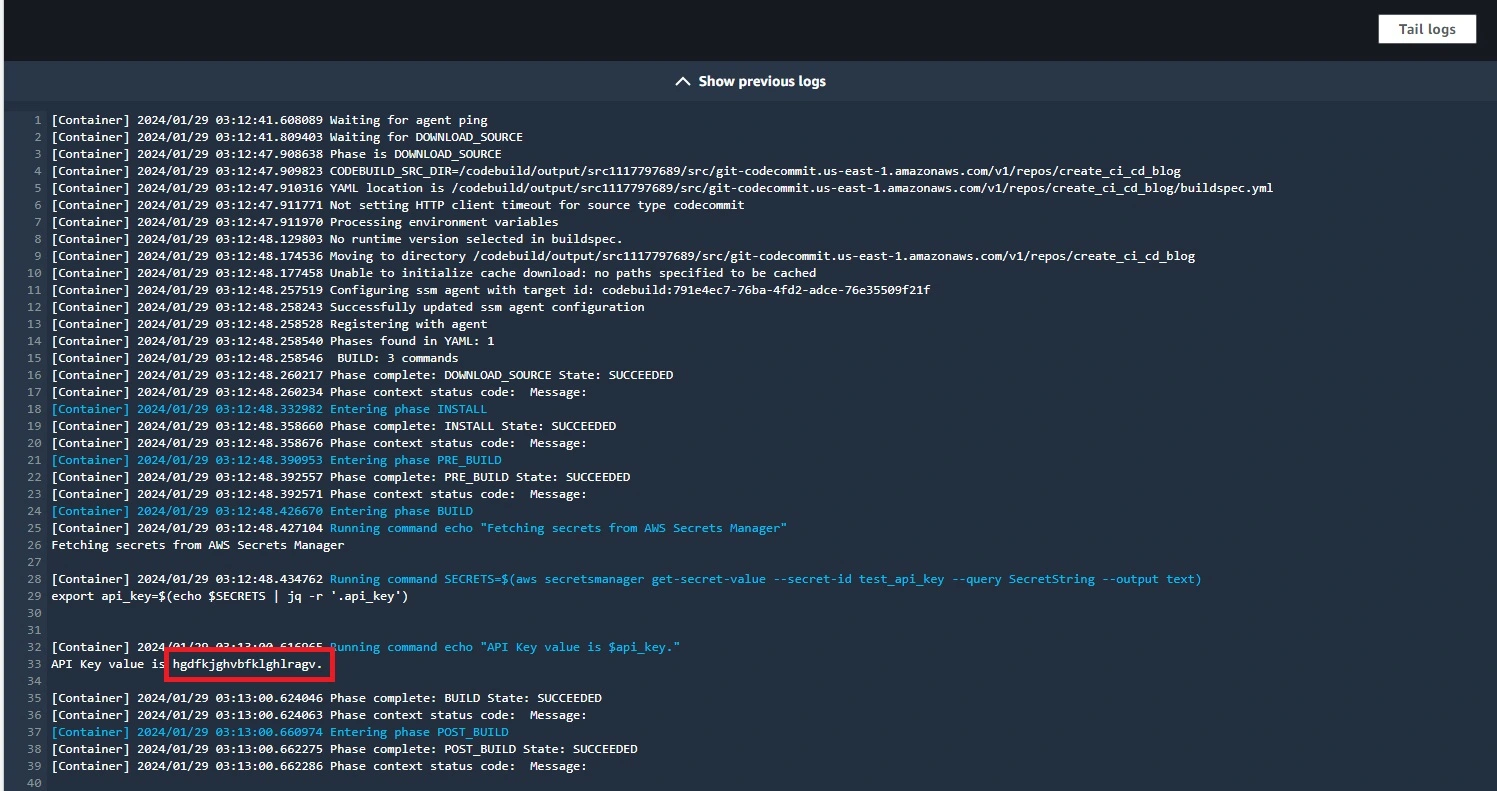
Step 4: Embrace Automation
Utilize the automated rotation feature of AWS Secrets Manager to enhance security. Periodically refreshing secrets provides an additional layer of protection for your application. Enable secret rotation by choosing intervals (hours/days/weeks/months) and selecting the associated Lambda function. In case the Lambda function is not present, you can easily create a new one directly from the console.
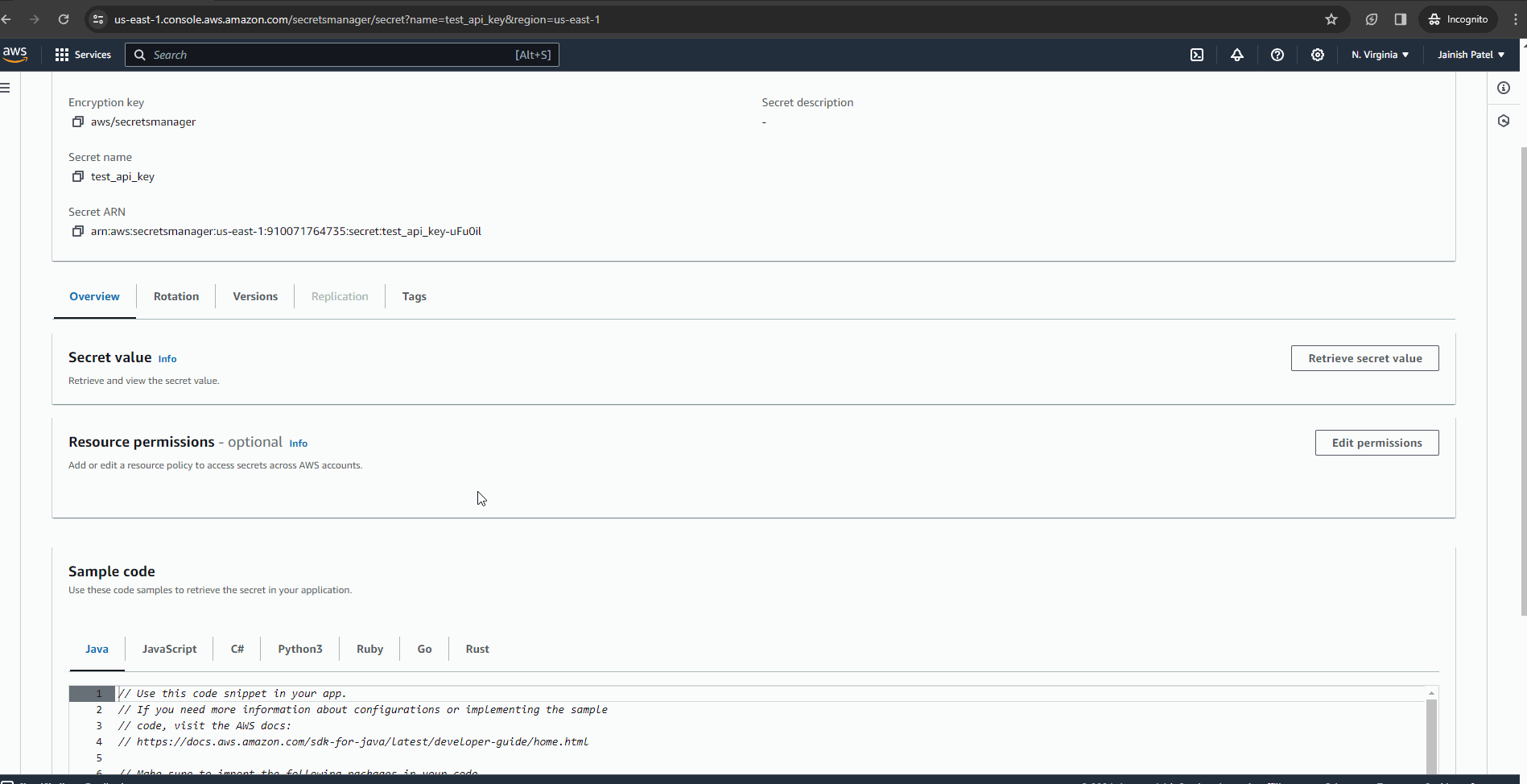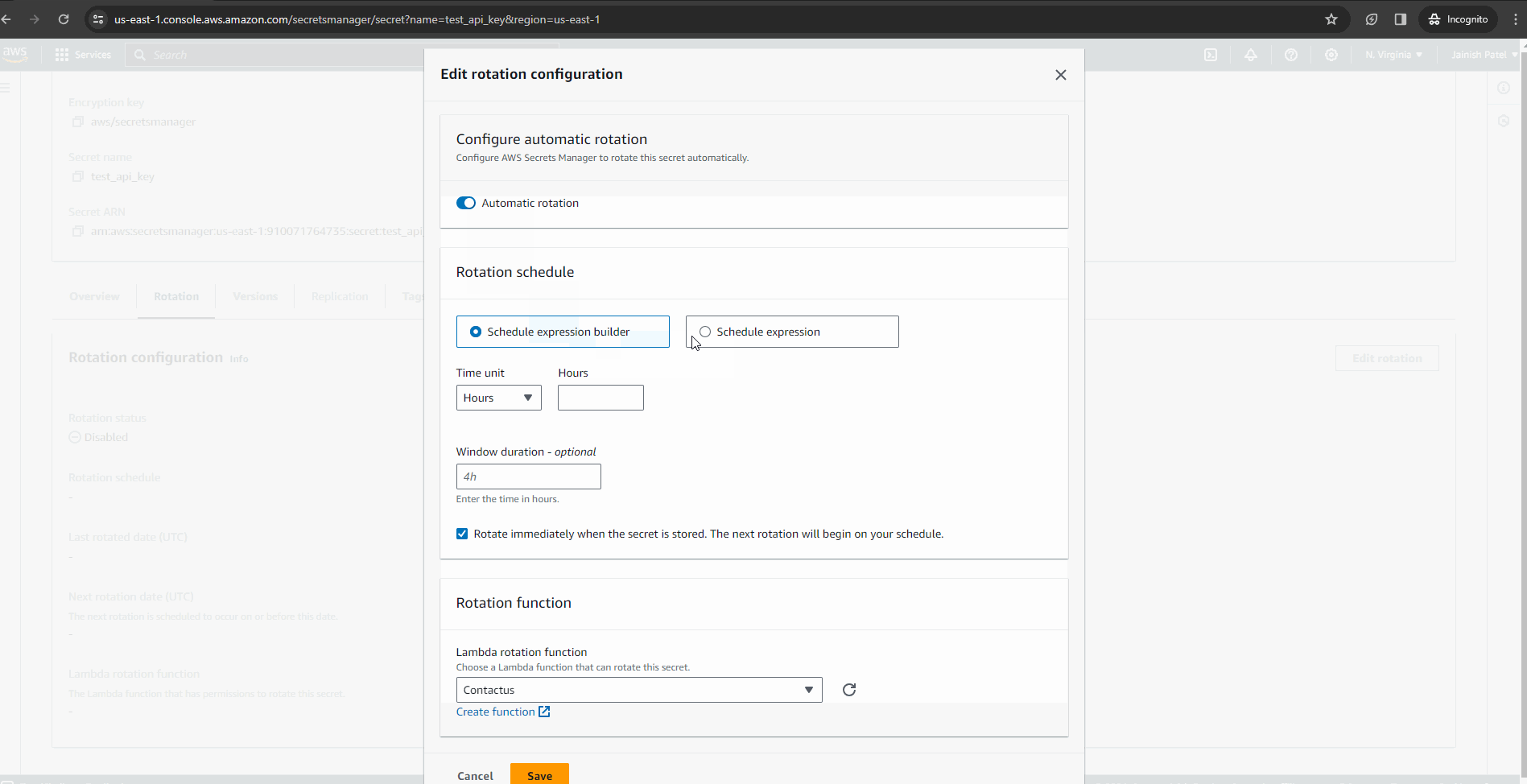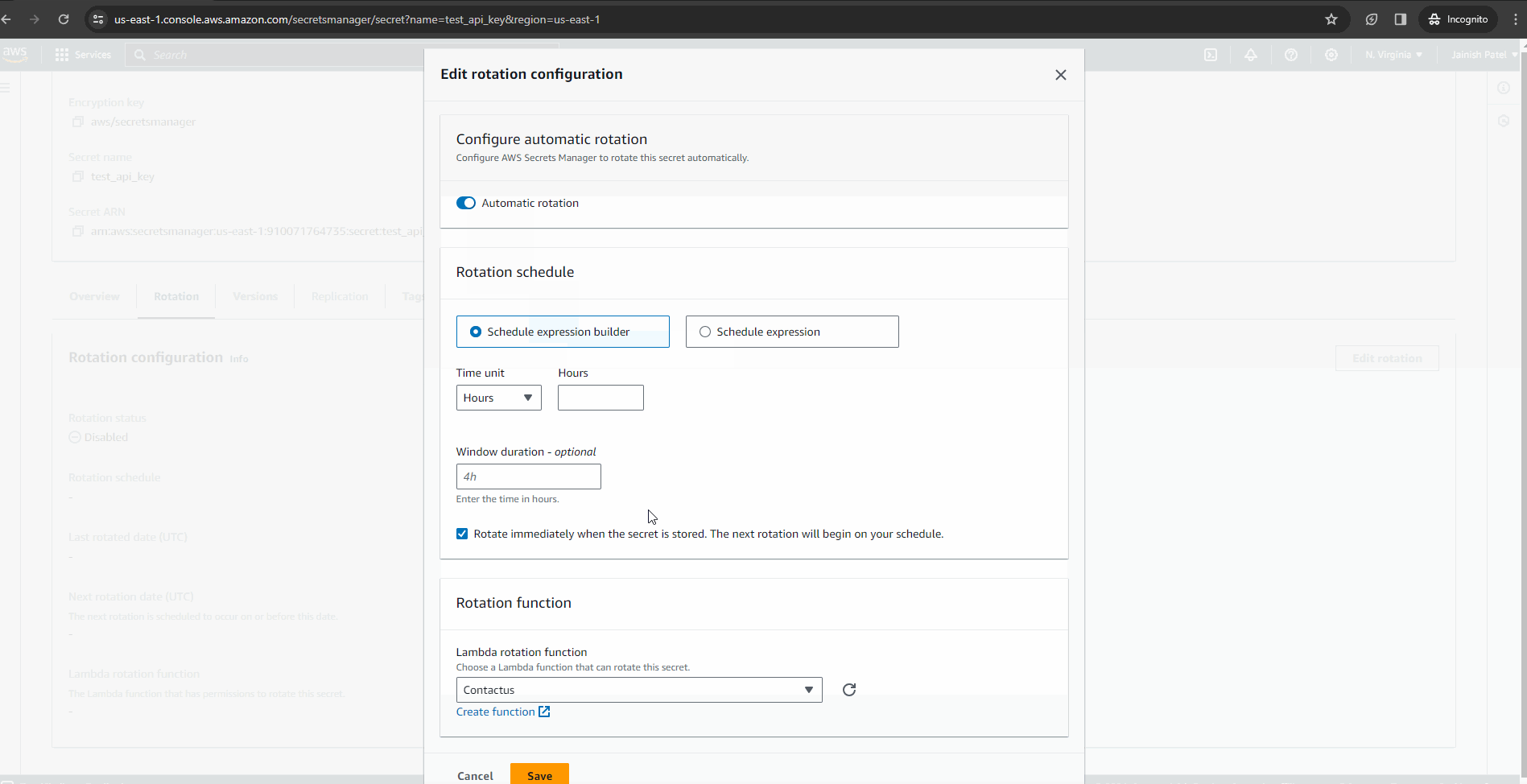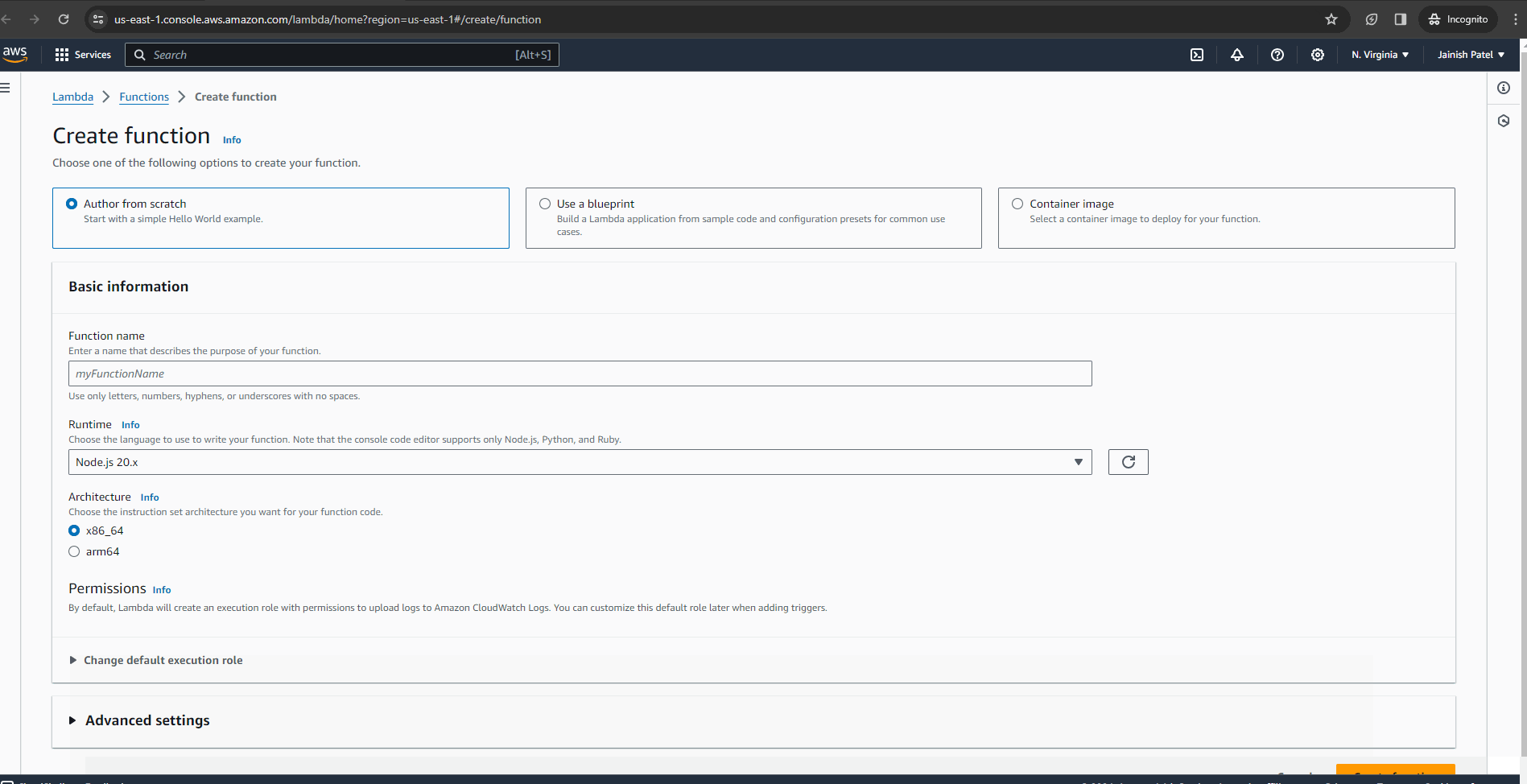
Conclusion: Secure Building Made Simple
Incorporating AWS Secrets Manager into your AWS CodeBuild workflow is a proactive step toward enhancing the security of your applications. This approach not only fortifies your application against potential threats but also simplifies the management of credentials and confidential data during your build and deployment pipeline.
Security is a shared responsibility. By following these best practices, you not only strengthen your security posture but also build with confidence in AWS CodeBuild.
